Design Analysis: Facebook Names Rules
Contents
6.8. Design Analysis: Facebook Names Rules#
We want to provide you, the reader, a chance to explore authenticity more, particularly considering how the rules built into social media platforms influence authenticity.
In this activity, you will be looking at Facebook’s name policy, and thinking through who this version of authenticity works for, and who it doesn’t1.
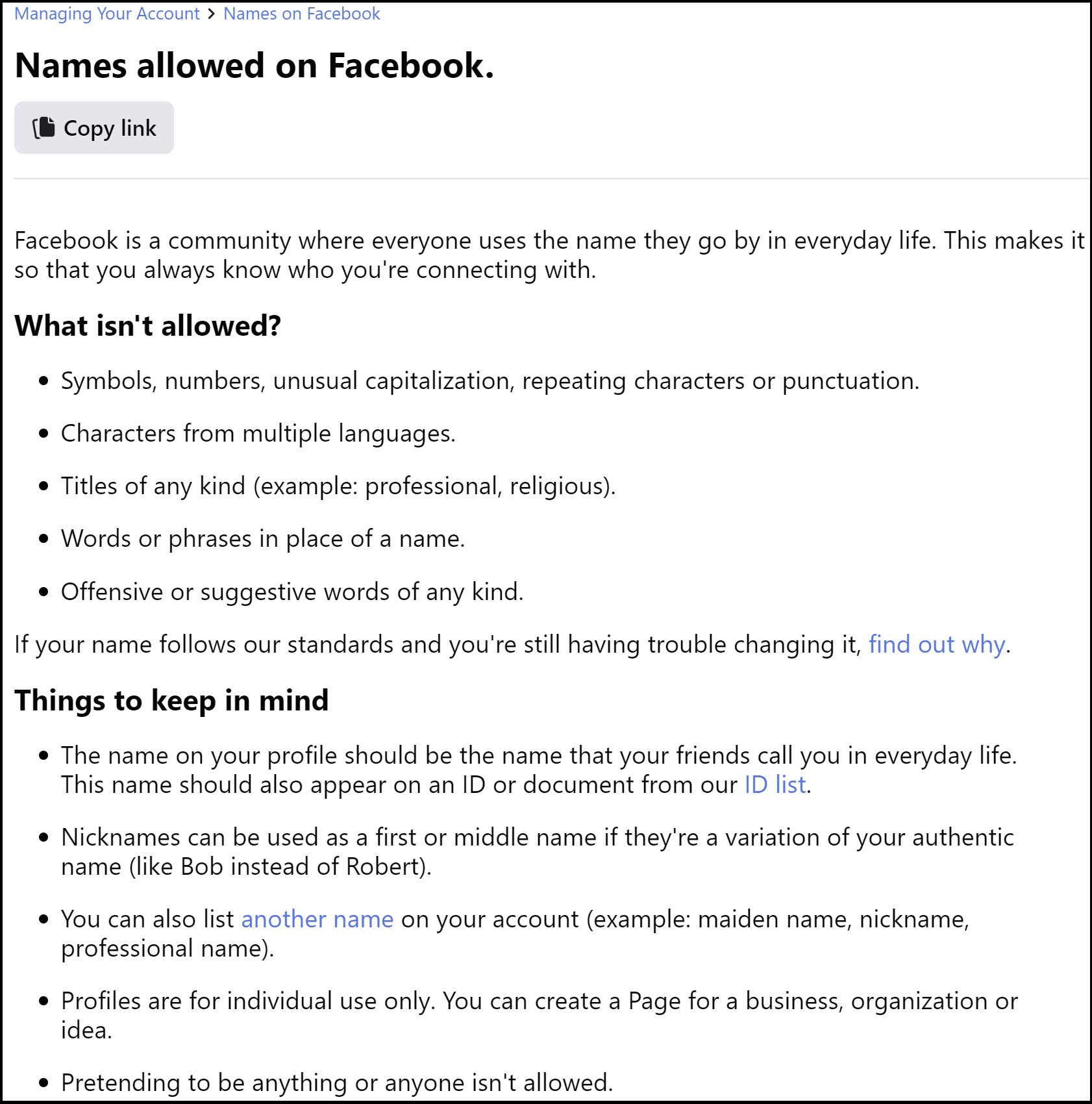
Fig. 6.9 The Facebook name policy as of 8/24/2022. You can see the current version here#
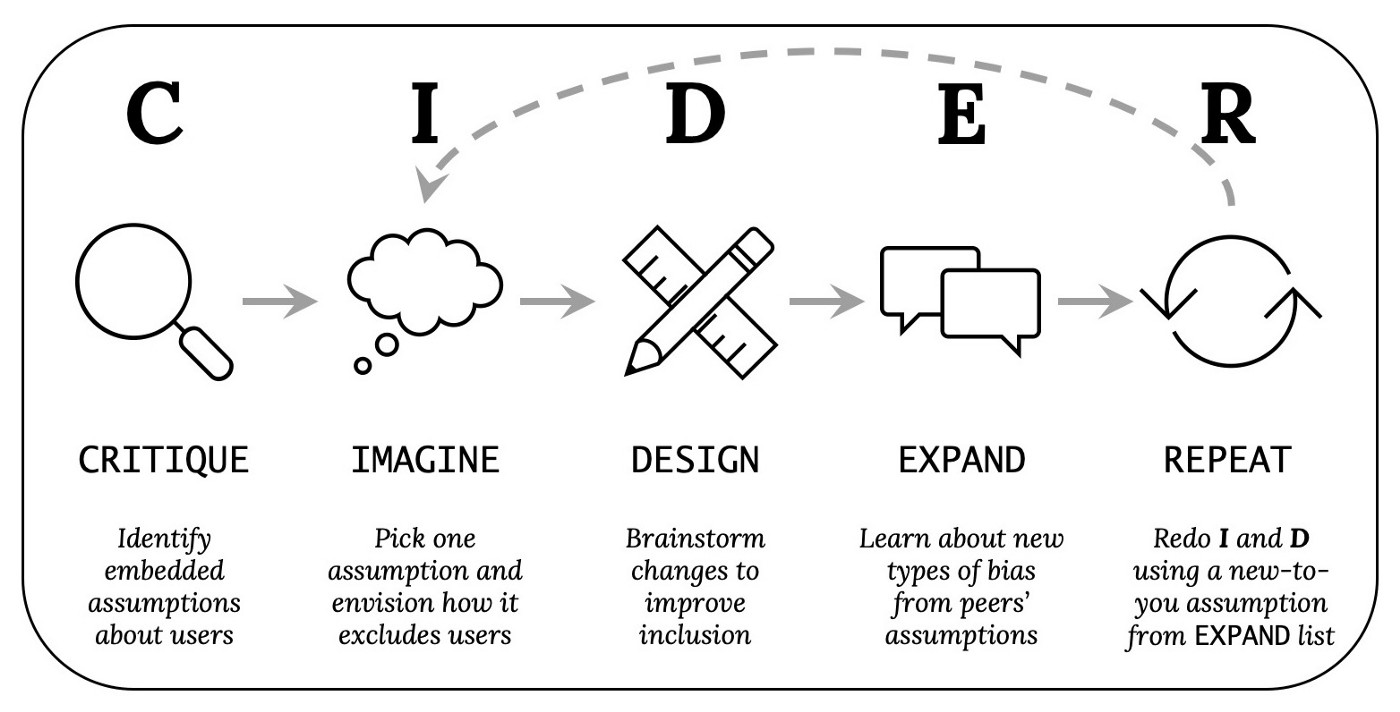
This activity follows the five-step CIDER method (Critique, Imagine, Design, Expand, Repeat), created by Alannah Oleson, et. al.. This activity works best if you can do it with others (like in a classroom), so you can learn from their observations as well.
So read through the Facebook name policy above (for this activity ignore clarifications or exceptions Facebook may have made elsewhere, since those weren’t deemed important enough to put on this main policy page). Then do the following (preferably on paper or in a blank computer document):
6.8.1. Critique (3-5 minutes, by yourself):#
What assumptions does Facebook’s name policy make about its users’ identities and their needs that might not be true or might cause problems? List as many as you can think of (bullet points encouraged).
If you are having trouble getting started, click to see some sample assumptions
Facebook assumes that accounts will be controlled by individuals (instead of e.g., families)
Facebook assumes a real name is safe to use (not necessarily true for some LGBTQIA people whose families might kick them out or political dissidents)
6.8.2. Imagine (2-3 minutes, by yourself):#
Select one of the above assumptions that you think is important to address. Then write a 1-2 sentence scenario where a user could not use Facebook as expected because of the assumption you selected. This represents one way the design could exclude certain users.
6.8.3. Design (3-5 minutes, by yourself):#
Brainstorm ways to change Facebook’s name policy to avoid the scenario you wrote above. List as many different kinds of potential solutions you can think of – aim for ten or more (bullet points encouraged).
6.8.4. Expand (5-10 minutes, with others):#
Combine your list of critiques with someone else’s (or if possible, have a whole class combine theirs).
You can also consider looking at the Wikipedia page on the Facebook real-name policy controversy
6.8.5. Repeat the Imagine and Design Tasks:#
Select another assumption from the list above that you think is important to address. Make sure to choose a different assumption than you used before. Choose one that you didn’t come up with yourself, if possible. Repeat the Imagine and Design steps.
- 1
You could also try this with different social media authenticity systems, like How to Get Verified on Bumble, which has the user take photos while mimicking poses.